and you may't exit out and return otherwise you drop a everyday living and your streak. And not long ago my super booster isn't really exhibiting up in each and every degree like it ought to
Clearly, That is an very lucrative venture for your DPRK. In 2024, a senior Biden administration official voiced worries that all over fifty% on the DPRK?�s international-currency earnings came from cybercrime, which includes its copyright theft pursuits, in addition to a UN report also shared claims from member states the DPRK?�s weapons plan is largely funded by its cyber operations.
Although you will find various tips on how to sell copyright, such as via Bitcoin ATMs, peer to see exchanges, and brokerages, generally quite possibly the most successful way is through a copyright Trade System.
The trades may possibly truly feel repetitive, while they've attempted to incorporate additional tracks later on inside the application (i like the Futures and selections). That's it. In general It truly is a great application that built me trade day-to-day for two mo. Leverage is straightforward and boosts are good. The bugs are exceptional and skip in a position.
When that?�s carried out, you?�re All set to convert. The precise methods to accomplish this process vary dependant upon which copyright System you use.
copyright.US is just not chargeable for any decline that you just may possibly incur from selling price fluctuations if you acquire, market, or maintain cryptocurrencies. Make sure you confer with our Conditions of Use To learn more.
Safety starts off with knowledge how developers gather and share your knowledge. Information privacy and protection techniques may perhaps vary dependant on your use, region, and age. The developer delivered this details and should update it after a while.
allow it to be,??cybersecurity measures may possibly come to be an afterthought, particularly when organizations deficiency the resources or staff for this kind of measures. The issue isn?�t exceptional to All those new to enterprise; on the other hand, even well-established organizations might Allow cybersecurity fall towards the wayside or may possibly deficiency the education and learning to be familiar with the speedily evolving menace landscape.
copyright exchanges change broadly during the providers they provide. Some platforms only supply a chance to acquire and offer, while others, like copyright.US, provide Innovative expert services Besides the basic principles, together with:
Also, response instances may be enhanced by making certain folks Performing throughout the agencies linked to blocking fiscal crime obtain coaching on copyright and how to leverage its ?�investigative ability.??Enter Code although signup to get $a hundred. Hey men Mj right here. I generally get started with the spot, so listed here we go: occasionally the application mechanic is complexed. The trade will go on its aspect the other way up (if you stumble upon an connect with) but it surely's rare.
The entire process of laundering and transferring copyright is expensive and includes fantastic friction, several of which happens to be deliberately produced by regulation enforcement plus some of it is actually inherent to the marketplace framework. As a result, the total achieving the North Korean govt will tumble much under $one.5 billion.
As soon as they had entry to Secure Wallet ?�s method, they manipulated the user interface (UI) that clientele like copyright staff would see. They replaced a benign JavaScript code with code designed to alter the supposed desired destination of your ETH during the wallet to wallets managed by North Korean operatives. This destructive code would only focus on distinct copyright wallets instead of wallets belonging to the varied other people of this platform, highlighting the specific mother nature of this attack.
The safety of your respective accounts is as imperative that you us as it is actually to you. That is why we give you these protection guidelines and simple practices you could observe to make certain your information will not fall into the incorrect arms.
These danger actors had been then ready to steal AWS session tokens, the short term keys that allow you to request short-term qualifications for your employer?�s AWS account. By hijacking Energetic tokens, the more info attackers have been in the position to bypass MFA controls and get use of Harmless Wallet ?�s AWS account. By timing their endeavours to coincide with the developer?�s regular function hours, they also remained undetected until eventually the particular heist.}
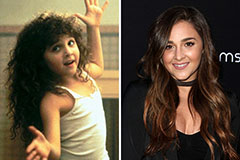 Alisan Porter Then & Now!
Alisan Porter Then & Now!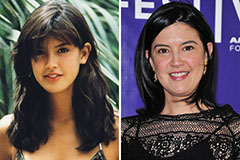 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Suri Cruise Then & Now!
Suri Cruise Then & Now! Bernadette Peters Then & Now!
Bernadette Peters Then & Now! Bill Murray Then & Now!
Bill Murray Then & Now!